DOWNLOAD :- PES 2012 Free APK DOWNLAOD
Wednesday, November 21, 2012
PES 2012 Free APK Downlaod
DOWNLOAD :- PES 2012 Free APK DOWNLAOD
PES 2012 – the unrivalled football experience on the Android platform!
FIFA 2012 Free APK Download
DOWNLOAD :- FIFA 2012 Free APK Download
Experience the action of your favorite sport like never before! Watch matches come to life with vibrant graphics and ultra-realistic animations.
** This is a big game, so we strongly recommend connecting to WiFi before downloading. We promise – it’s worth it! **
REAL PLAYERS, REAL TEAMS, REAL LEAGUES
Featuring over 22 officially licensed leagues, 500+ licensed teams and more than 15,000 players. Take to the pitch with superstars like Kaka, Wayne Rooney, Gerard Piqué, Karim Benzema and more. From the English Premiership and La Liga, to the German Bundesliga and beyond – dominate your league and march toward glory in 32 authentic stadiums.
Need for Speed™ Most Wanted Free APK Download
DOWNLOAD :- Need for Speed™ Most Wanted Free APK Download
The graphics are absolutely awesome”
“It pushes the mobile platform to its utmost limits and doesn’t even break a sweat” (Capsule Computers)
Buckle up, hit the gas and hold on tight; you’re in for the ride of your life. Outrun cops, outsmart rivals – and outdrive your friends – in the most dangerous Need for Speed yet. Do you dare to be the Most Wanted?
** Need for Speed™ Most Wanted is an immersive, high quality game that requires a 550MB+ download. To speed things up, we recommend connecting to WiFi.**
Friday, November 16, 2012
How To Trust a PC In WINDOWS 8
Many people got obstacle after installed the Windows 8 . Windows 8 requires Trusted PC user . So here is the way to Trust your PC for windows .Follow the steps carefully!
1. To trust your PC after signing into Windows 8 for the first time, open the Action Center or the settings bar(That open from right side)and click the Trust this PC link.You can also mouse over the bottom or top right corners of your screen, click the Settings > select Change PC Settings.
OR
2. Click the Trust this PC link on behind the Users
3.After logging in with the Microsoft account you’re using with Windows 8, you’ll be able to enter the security code Microsoft sent you. This code may be sent to your email address or your cell phone, depending on the recovery information you provided while setting up your Microsoft account.
4.You can click the I didn’t get the code to have Microsoft send you the security code at an email or phone number of your choice. If you don’t have access to a cell phone, Microsoft can also call a landline phone instead of sending a text message.
5.If you were emailed a security confirmation, you can also click the Confirm button in the email you received from the Microsoft account team.
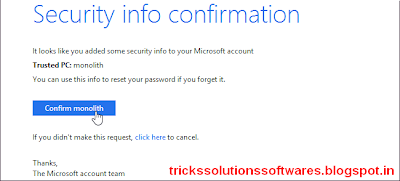
6. Click the button or enter the code and your computer will be confirmed as trusted for your Microsoft account.
1. To trust your PC after signing into Windows 8 for the first time, open the Action Center or the settings bar(That open from right side)and click the Trust this PC link.You can also mouse over the bottom or top right corners of your screen, click the Settings > select Change PC Settings.
OR
2. Click the Trust this PC link on behind the Users
3.After logging in with the Microsoft account you’re using with Windows 8, you’ll be able to enter the security code Microsoft sent you. This code may be sent to your email address or your cell phone, depending on the recovery information you provided while setting up your Microsoft account.
4.You can click the I didn’t get the code to have Microsoft send you the security code at an email or phone number of your choice. If you don’t have access to a cell phone, Microsoft can also call a landline phone instead of sending a text message.
5.If you were emailed a security confirmation, you can also click the Confirm button in the email you received from the Microsoft account team.

6. Click the button or enter the code and your computer will be confirmed as trusted for your Microsoft account.
From the Security Info page on Microsoft’s account management website, you can view your trusted PCs and delete trusted PCs. You can also manage your phone numbers, alternate email addresses, and security questions from here.
ALL About Spyware
There are a lot of PC users that know little about "Spyware", "Mal-ware", "hijackers", "Dialers" & many more. This will help you avoid pop-ups, spammers and all those baddies.
What is spy-ware?
Spy-ware is Internet jargon for Advertising Supported software (Ad-ware). It is a way for shareware authors to make money from a product, other than by selling it to the users. There are several large media companies that offer them to place banner ads in their products in exchange for a portion of the revenue from banner sales. This way, you don't have to pay for the software and the developers are still getting paid. If you find the banners annoying, there is usually an option to remove them, by paying the regular licensing fee.
Known spywares
There are thousands out there, new ones are added to the list everyday. But here are a few:
Alexa, Aureate/Radiate, BargainBuddy, ClickTillUWin, Conducent Timesink, Cydoor, Comet Cursor, eZula/KaZaa Toptext, Flashpoint/Flashtrack, Flyswat, Gator, GoHip, Hotbar, ISTbar, Lions Pride Enterprises/Blazing Logic/Trek Blue, Lop (C2Media), Mattel Brodcast, Morpheus, NewDotNet, Realplayer, Songspy, Xupiter, Web3000, WebHancer, Windows Messenger Service.
How to check if a program has spyware?
The is this Little site that keeps a database of programs that are known to install spyware.
Check Here: http://www.spywareguide.com/product_search.php
If you would like to block pop-ups (IE Pop-ups).
There tons of different types out there, but these are the 2 best, i think.
Try: Google Toolbar (http://toolbar.google.com/) This program is Free
Try: AdMuncher (http://www.admuncher.com) This program is Shareware
If you want to remove the "spyware" try these.
Try: Lavasoft Ad-Aware (http://www.lavasoftusa.com/) This program is Free
Info: Ad-aware is a multi spyware removal utility, that scans your memory, registry and hard drives for known spyware components and lets you remove them. The included backup-manager lets you reinstall a backup, offers and multi language support.
Try: Spybot-S&D (http://www.safer-networking.org/) This program is Free
Info: Detects and removes spyware of different kinds (dialers, loggers, trojans, user tracks) from your computer. Blocks ActiveX downloads, tracking cookies and other threats. Over 10,000 detection files and entries. Provides detailed information about found problems.
Try: BPS Spyware and Adware Remover (http://www.bulletproofsoft.com/spyware-remover.html) This program is Shareware
Info: Adware, spyware, trackware and big brotherware removal utility with multi-language support. It scans your memory, registry and drives for known spyware and lets you remove them. Displays a list and lets you select the items you'd like to remove.
Try: Spy Sweeper v2.2 (http://www.webroot.com/wb/products/spysweeper/index.php) This program is Shareware
Info: Detects and removes spyware of different kinds (dialers, loggers, trojans, user tracks) from your computer.
The best scanner out there, and updated all the time.
Try: HijackThis 1.97.7 (http://www.spywareinfo.com/~merijn/downloads.html) This program is Freeware
Info: HijackThis is a tool, that lists all installed browser add-on, buttons, startup items and allows you to inspect them, and optionally remove selected items.
If you would like to prevent "spyware" being install.
Try: SpywareBlaster 2.6.1 (http://www.wilderssecurity.net/spywareblaster.html) This program is Free
Info: SpywareBlaster doesn`t scan and clean for so-called spyware, but prevents it from being installed in the first place. It achieves this by disabling the CLSIDs of popular spyware ActiveX controls, and also prevents the installation of any of them via a webpage.
Try: SpywareGuard 2.2 (http://www.wilderssecurity.net/spywareguard.html) This program is Free
Info: SpywareGuard provides a real-time protection solution against so-called spyware. It works similar to an anti-virus program, by scanning EXE and CAB files on access and alerting you if known spyware is detected.
Try: XP-AntiSpy (http://www.xp-antispy.org/) This program is Free
Info: XP-AntiSpy is a small utility to quickly disable some built-in update and authentication features in WindowsXP that may rise security or privacy concerns in some people.
Try: SpySites (http://camtech2000.net/Pages/SpySites_Prog...ml#SpySitesFree) This program is Free
Info: SpySites allows you to manage the Internet Explorer Restricted Zone settings and easily add entries from a database of 1500+ sites that are known to use advertising tracking methods or attempt to install third party software.
If you would like more Information about "spyware".
Check these sites.
http://www.spychecker.com/
http://www.spywareguide.com/
http://www.cexx.org/adware.htm
http://www.theinfomaniac.net/infomaniac/co...rsSpyware.shtml
http://www.thiefware.com/links/
http://simplythebest.net/info/spyware.html
Usefull tools...
Try: Stop Windows Messenger Spam 1.10 (http://www.jester2k.pwp.blueyonder.co.uk/j...r2ksoftware.htm) This program is Free
Info: "Stop Windows Messenger Spam" stops this Service from running and halts the spammers ability to send you these messages.
----------------------------------------------------------------------------
All these softwares will help remove and prevent evil spammers and spywares attacking your PC. I myself recommend getting "spyblaster" "s&d spybot" "spy sweeper" & "admuncher" to protect your PC. A weekly scan is also recommended
Free Virus Scan
Scan for spyware, malware and keyloggers in addition to viruses, worms and trojans. New threats and annoyances are created faster than any individual can keep up with.
http://defender.veloz.com// - 15k
Finding . is a Click Away at 2020Search.com
Having trouble finding what you re looking for on: .? 2020Search will instantly provide you with the result you re looking for by drawing on some of the best search engines the Internet has to offer. Your result is a click away!
http://www.2020search.com// - 43k
What is spy-ware?
Spy-ware is Internet jargon for Advertising Supported software (Ad-ware). It is a way for shareware authors to make money from a product, other than by selling it to the users. There are several large media companies that offer them to place banner ads in their products in exchange for a portion of the revenue from banner sales. This way, you don't have to pay for the software and the developers are still getting paid. If you find the banners annoying, there is usually an option to remove them, by paying the regular licensing fee.
Known spywares
There are thousands out there, new ones are added to the list everyday. But here are a few:
Alexa, Aureate/Radiate, BargainBuddy, ClickTillUWin, Conducent Timesink, Cydoor, Comet Cursor, eZula/KaZaa Toptext, Flashpoint/Flashtrack, Flyswat, Gator, GoHip, Hotbar, ISTbar, Lions Pride Enterprises/Blazing Logic/Trek Blue, Lop (C2Media), Mattel Brodcast, Morpheus, NewDotNet, Realplayer, Songspy, Xupiter, Web3000, WebHancer, Windows Messenger Service.
How to check if a program has spyware?
The is this Little site that keeps a database of programs that are known to install spyware.
Check Here: http://www.spywareguide.com/product_search.php
If you would like to block pop-ups (IE Pop-ups).
There tons of different types out there, but these are the 2 best, i think.
Try: Google Toolbar (http://toolbar.google.com/) This program is Free
Try: AdMuncher (http://www.admuncher.com) This program is Shareware
If you want to remove the "spyware" try these.
Try: Lavasoft Ad-Aware (http://www.lavasoftusa.com/) This program is Free
Info: Ad-aware is a multi spyware removal utility, that scans your memory, registry and hard drives for known spyware components and lets you remove them. The included backup-manager lets you reinstall a backup, offers and multi language support.
Try: Spybot-S&D (http://www.safer-networking.org/) This program is Free
Info: Detects and removes spyware of different kinds (dialers, loggers, trojans, user tracks) from your computer. Blocks ActiveX downloads, tracking cookies and other threats. Over 10,000 detection files and entries. Provides detailed information about found problems.
Try: BPS Spyware and Adware Remover (http://www.bulletproofsoft.com/spyware-remover.html) This program is Shareware
Info: Adware, spyware, trackware and big brotherware removal utility with multi-language support. It scans your memory, registry and drives for known spyware and lets you remove them. Displays a list and lets you select the items you'd like to remove.
Try: Spy Sweeper v2.2 (http://www.webroot.com/wb/products/spysweeper/index.php) This program is Shareware
Info: Detects and removes spyware of different kinds (dialers, loggers, trojans, user tracks) from your computer.
The best scanner out there, and updated all the time.
Try: HijackThis 1.97.7 (http://www.spywareinfo.com/~merijn/downloads.html) This program is Freeware
Info: HijackThis is a tool, that lists all installed browser add-on, buttons, startup items and allows you to inspect them, and optionally remove selected items.
If you would like to prevent "spyware" being install.
Try: SpywareBlaster 2.6.1 (http://www.wilderssecurity.net/spywareblaster.html) This program is Free
Info: SpywareBlaster doesn`t scan and clean for so-called spyware, but prevents it from being installed in the first place. It achieves this by disabling the CLSIDs of popular spyware ActiveX controls, and also prevents the installation of any of them via a webpage.
Try: SpywareGuard 2.2 (http://www.wilderssecurity.net/spywareguard.html) This program is Free
Info: SpywareGuard provides a real-time protection solution against so-called spyware. It works similar to an anti-virus program, by scanning EXE and CAB files on access and alerting you if known spyware is detected.
Try: XP-AntiSpy (http://www.xp-antispy.org/) This program is Free
Info: XP-AntiSpy is a small utility to quickly disable some built-in update and authentication features in WindowsXP that may rise security or privacy concerns in some people.
Try: SpySites (http://camtech2000.net/Pages/SpySites_Prog...ml#SpySitesFree) This program is Free
Info: SpySites allows you to manage the Internet Explorer Restricted Zone settings and easily add entries from a database of 1500+ sites that are known to use advertising tracking methods or attempt to install third party software.
If you would like more Information about "spyware".
Check these sites.
http://www.spychecker.com/
http://www.spywareguide.com/
http://www.cexx.org/adware.htm
http://www.theinfomaniac.net/infomaniac/co...rsSpyware.shtml
http://www.thiefware.com/links/
http://simplythebest.net/info/spyware.html
Usefull tools...
Try: Stop Windows Messenger Spam 1.10 (http://www.jester2k.pwp.blueyonder.co.uk/j...r2ksoftware.htm) This program is Free
Info: "Stop Windows Messenger Spam" stops this Service from running and halts the spammers ability to send you these messages.
----------------------------------------------------------------------------
All these softwares will help remove and prevent evil spammers and spywares attacking your PC. I myself recommend getting "spyblaster" "s&d spybot" "spy sweeper" & "admuncher" to protect your PC. A weekly scan is also recommended
Free Virus Scan
Scan for spyware, malware and keyloggers in addition to viruses, worms and trojans. New threats and annoyances are created faster than any individual can keep up with.
http://defender.veloz.com// - 15k
Finding . is a Click Away at 2020Search.com
Having trouble finding what you re looking for on: .? 2020Search will instantly provide you with the result you re looking for by drawing on some of the best search engines the Internet has to offer. Your result is a click away!
http://www.2020search.com// - 43k
Monday, March 5, 2012
How to modify *.exe files
learn how to change *.exe files, in 5 easy steps:
1) Don't try to modify a prog by editing his source in a dissasembler.Why?
Cause that's for programmers and assembly experts only.
try to view it in hex you'll only get tons of crap you don't understand.
First off, you need Resource Hacker(last version). It's a resource editor-
very easy to use, You can download it at h**p://www.users.on.net/johnson/resourcehacker/
2) Unzip the archive, and run ResHacker.exe. You can check out the help file too
3) You will see that the interface is simple and clean. Go to the menu FileOpen or press Ctrl+O to open a file. Browse your way to the file you would like to edit. You can edit *.exe, *.dll, *.ocx, *.scr and *.cpl files, but this tutorial is to teach you how to edit *.exe files, so open one.
4) In the left side of the screen a list of sections will appear.
The most common sections are
-String table;
-RCData;
-Dialog;
-Cursor group;
-Bitmap;
-WAV.
*Icon: You can wiew and change the icon(s) of the program by double-clicking the icon section,chossing the icon, right-clicking on it an pressing "replace resource". After that you can choose the icon you want to replace the original with.
*String table: a bunch of crap, useful sometimes, basic programming knowladge needed.
*RCData: Here the real hacking begins. Modify window titles, buttons, text, and lots more!
*Dialog:Here you can modify the messages or dialogs that appear in a program. Don't forget to press "Compile" when you're done!
*Cursor group: Change the mouse cursors used in the program just like you would change the icon.
*Bitmap: View or change images in the programs easy!
*WAV:Change the sounds in the prog. with your own.
5) In the RCData,Dialog,Menu and String table sections you can do a lot of changes. You can modify or translate the text change links, change buttons, etc.
TIP: To change a window title, search for something like: CAPTION "edit this".
TIP: After all operations press the "Compile Script" button, and when you're done editing save, your work @ FileSave(Save as).
TIP: When you save a file,the original file will be backed up by default and renamed to Name_original and the saved file will have the normal name of the changed prog.
TIP: Sometimes you may get a message like: "This program has a non-standard resource layout... it has probably been compressed with an .EXE compressor." That means that Resource Hacker can't modify it because of it's structure.
how To Hide Yourself From Network Users!, And give access to only specific users!
How to Hide in the (Network) Neighborhood
Don't want your XP computer to show up in the network browse list (Network Neighborhood/My Network Places) to other users on your network? One way to accomplish that is to disable file sharing. To do this, click Start, right click My Network Places and select Properties. Right click your local area connection and click Properties. Uncheck the box that says File and Printer Sharing for Microsoft Networks. Click OK.
But what if you want to be able to share folders with some users; you just don't want everyone on the network to see your computer's shares? There's a way:
Click Start and select Run.
In the Run box, type net config server /hidden:yes
Click OK.
Now others who know the UNC path (\\computer name\share name) can connect to your computer's shares from the Run box, but it won't show up in the network browse list.
Don't want your XP computer to show up in the network browse list (Network Neighborhood/My Network Places) to other users on your network? One way to accomplish that is to disable file sharing. To do this, click Start, right click My Network Places and select Properties. Right click your local area connection and click Properties. Uncheck the box that says File and Printer Sharing for Microsoft Networks. Click OK.
But what if you want to be able to share folders with some users; you just don't want everyone on the network to see your computer's shares? There's a way:
Click Start and select Run.
In the Run box, type net config server /hidden:yes
Click OK.
Now others who know the UNC path (\\computer name\share name) can connect to your computer's shares from the Run box, but it won't show up in the network browse list.
Debug: Learn how to crack windows, programs ect manually
Debug is a program that comes with modern versions of DOS (I do not know when I started shipping out with DOS). Anyway, all Windows users should have it already.
It's a great tool for debuging programs, unassembling and cracking, and reading "hidden" memory areas like the boot sector, and much more.
The following was copied from an assembly tutorial who's author we cannot credit, because we have no idea who he is.
Get into DOS and type "debug", you will get a prompt like this:
-
now type "?", you should get the following response:
assemble A [address]
compare C range address
dump D [range]
enter E address [list]
fill F range list
go G [=address] [addresses]
hex H value1 value2
input I port
load L [address] [drive] [firstsector] [number]
move M range address
name N [pathname] [arglist]
output O port byte
proceed P [=address] [number]
quit Q
register R [register]
search S range list
trace T [=address] [value]
unassemble U [range]
write W [address] [drive] [firstsector] [number]
allocate expanded memory XA [#pages]
deallocate expanded memory XD [handle]
map expanded memory pages XM [Lpage] [Ppage] [handle]
display expanded memory status XS
Lets go through each of these commands:
Assemble:
-a
107A:0100
At this point you can start assembling some programs, just like using a assembler. However the debug assembler is very limited as you will probably notice. Lets try to enter a simple program:
-a
107A:0100 MOV AH,02
107A:0102 MOV DL,41
107A:0104 INT 21
107A:0106 INT 20
-g
A
Program terminated normally
That's the same program we did at the end of the previous chapter. Notice how you run the program you just entered with "g", and also notice how the set-up part is not there? That's because debug is just too limited to support that.
Another thing you can do with assemble is specify the address at which you want to start, by default this is 0100 since that's where all .COM files start.
Compare:
Compare takes 2 block of memory and displays them side by side, byte for byte. Lets do an example. Quite out of debug if you haven't already using "q". Now type "debug c:\command.com"
-c 0100 l 8 0200
10A3:0100 7A 06 10A3:0200
This command compared offset 0100 with 0200 for a length of 8 bytes. Debug responded with the location that was DIFFERENT. If 2 locations were the same, debug would just omit them, if all are the same debug would simply return to the prompt without any response.
Dump:
Dump will dump a specified memory segment. To test it, code that assembly program again:
C:\>debug
-a
107A:0100 MOV AH,02
107A:0102 MOV DL,41
107A:0104 INT 21
107A:0106 INT 20
-d 0100 l 8
107A:0100 B4 02 B2 41 CD 21 CD 20
...A.!.
The "B4 02 B2 41 CD 21 CD 20" is the program you just made in machine language.
B4 02 = MOV AH,02
B2 41 = MOV DL,41
CD 21 = INT 21
CD 20 = INT 20
The "...A.!." part is your program in ASCII. The "." represent non-printable characters. Notice the A in there.
Enter:
This is one of the hard commands. With it you can enter/change certain memory areas. Lets change our program so that it prints a B instead of an A.
-e 0103 <-- edit program at segment 0103
107A:0103 41.42 <-- change 41 to 42
-g
B
Program terminated normally
-
Wasn't that amazing?
Fill:
This command is fairly useless, but who knows....
It fills the specified amount of memory with the specified data. Lets for example clear out all memory from segment 0100 to 0108, which happens to be our program.
-f 0100 l 8 0 <-- file offset 0100 for a length of 8 bytes with 0
-d 0100 l 8 <-- verify that it worked
107A:0100 00 00 00 00 00 00 00 00 .......
Yep, it worked.
Go:
So far we used go (g) to start the program we just created. But Go can be used for much more. For example, lets say we want to execute a program at 107B:0100:
-r CS <-- set the CS register to point to 107B
CS 107A
:107B
-g =100
You can also set breakpoints.
-a <-- enter our original program so we have something
107A:0100 MOV AH,02 to work with
107A:0102 MOV DL,41
107A:0104 INT 21
107A:0106 INT 20
-g 102 <-- set up a break point at 107A:0102
At this point the program will stop, display all registers and the current instruction.
Hex:
This can be very useful. It subtracts and adds two hexadecimal values:
-h 2 1
0003 0001 <-- 2h + 1+ = 3h and 2h - 1h = 1h
This is very useful for calculating a programs length, as you will see later.
Input:
This is one of the more advanced commands, and I decided not to talk about it too much for now. It will read a byte of data from any of your computers I/O ports (keyboard, mouse, printer, etc).
-i 3FD
60
-
Your data may be different.
In case you want to know, 3FD is Com port 1, also known as First Asynchronous Adapter.
Load:
This command has 2 formats. It can be used to load the filename specified with the name command (n), or it can load a specific sector.
-n c:\command.com
-l
This will load command.com into debug. When a valid program is loaded all registers will be set up and ready to execute the program.
The other method is a bit more complicated, but potential also more usefull. The syntax is
L <address> <drive letter/> <sector> <amount to load>
-l 100 2 10 20
This will load starting at offset 0100 from drive C (0 = A, 1 = B, 2 = C, etc), sector 10h for 20h sectors. This can be useful for recovering files you deleted.
Move:
Move takes a byte from the starting address and moves it to the destination address. This is very good to temporary move data into a free area, than manipulate it without having to worry about affecting the original program. It is especially useful if used in conjunction with the r command to which I will get later. Lets try an example:
-a <-- enter our original program so we have something
107A:0100 MOV AH,02 to work with
107A:0102 MOV DL,41
107A:0104 INT 21
107A:0106 INT 20
-m 107A:0100 L 8 107B:0100 <-- more 8 bytes starting from 107A:0100 into 107B:0100
-e 107B:0103 <-- edit 107B:0103
107B:0103 41.42 <-- and change it 42 (
-d 107A:0100 L 8 <-- make sure it worked
107A:0100 B4 02 B2 41 CD 21 CD 20 ...A.!.
-d 107B:0100 L 8
107A:0100 B4 02 B2 42 CD 21 CD 20 ...B.!.
-m 107B:0100 L 8 107A:0100 <-- restore the original program since we like the changes.
Name:
This will set debug up with a filename to use for I/O commands. You have to include the file extension, and you may use addition commands:
-n c:\command.com
Output:
Exactly what you think it is. Output sends stuff to an I/O port. If you have an external modem with those cool lights on it, you can test this out. Find out what port your modem is on and use the corresponding hex number below:
Com 1 = 3F8 - 3FF (3DF for mine)
Com 2 = 2F8 - 2FF
Com 3 = ??? - ??? (if someone knows, please let me know)
Now turn on the DTA (Data Terminal Ready) bit by sending 01h to it:
-o XXX 1 <-- XXX is the com port in hex
As soon as you hit enter, take a look at your modem, you should see a light light up. You can have even more fun with the output command. Say someone put one of those BIOS passwords on "your" computer. Usually you'd have to take out the battery to get rid of it, but not anymore:
MI/AWARD BIOS
-o 70 17
-o 71 17
QPHOENIX BIOS
-o 70 FF
-o 71 17
QGENERIC
-o 70 2E
-o 71 FF
These commands will clear the BIOS memory, thus disabling the password.
Proceed:
Proceeds in the execution of a program, usually used together withy Trace, which I will cover later. Like the go command, you can specify an address from which to start
using =address
-p 2
Debug will respond with the registers and the current command to be executed.
Quite:
This has got to be the most advanced feature of debug, it exits debug!
-q
Register:
This command can be used to display the current value of all registers, or to manually set them. This is very useful for writing files as you will see later on.
-r AX
AX: 011B
:5
-
Search:
Another very useful command. It is used to find the occurrence of a specific byte, or series of bytes in a segment. The data to search for can by either characters, or a hex value. Hex values are entered with a space or comma in between them, and characters are enclosed with quotes (single or double). You can also search for hex and characters with the same string:
-n c:\command.com <-- load command.com so we have some data to search in
-l
-s 0 l 0 "MS-DOS" <-- search entire memory block for "MS-DOS"
10A3:39E9 <-- found the string in 10A3:39E9
NOTE: the search is case sensitive!
Trace:
This is a truly great feature of debug. It will trace through a program one instruction at a time, displaying the instruction and registers after each. Like the go command you can specify where to start executing from, and for how long.
-a <-- yes, this thing again
107A:0100 MOV AH,02
107A:0102 MOV DL,41
107A:0104 INT 21
107A:0106 INT 20
-t =0100 8
If you leave out the amount of instructions that you want to trace, you can use the proceed (p) to continue the execution as long as you want.
Unassemble:
Unassembles a block of code. Great for debugging (and cracking)
-u 100 L 8 <-- unassembles 8 bytes starting at offset 100
107A:0100 MOV AH,02 <-- debut's response
107A:0102 MOV DL,41
107A:0104 INT 21
107A:0106 INT 20
Write:
This command works very similar to Load. It also has 2 ways it can operate: using name, and by specifying an exact location. Refer to back to Load for more information.
NOTE: The register CX must be set the file size in order to write!
NOTE: Write will not write .EXE or .HEX files.[SIZE=7][SIZE=14]
How to Matinence Computer
You may not realize it, but your computer and your car have something in common: they both need regular maintenance. No, you don't need to change your computer's oil. But you should be updating your software, keeping your antivirus subscription up to date, and checking for spyware. Read on to learn what you can do to help improve your computer's security.
Getting started
Here are some basics maintenance tasks you can do today to start improving your computer's security. Be sure you make these part of your ongoing maintenance as well.
* Sign up for software update e-mail notices. Many software companies will send you e-mail whenever a software update is available. This is particularly important for your operating system (e.g., Microsoft VV!|VD0VV$® or Macintosh), your antivirus program, and your firewall.
* Register your software. If you still have registration forms for existing software, send them in. And be sure to register new software in the future. This is another way for the software manufacturer to alert you when new updates are available.
* Install software updates immediately.
When you get an update notice, download the update immediately and install it. (Remember, downloading and installing are two separate tasks.)
An ounce of prevention
A few simple steps will help you keep your files safe and clean.
* Step 1: Update your software
* Step 2: Backup your files
* Step 3: Use antivirus software and keep it updated
* Step 4: Change your passwords
Developing ongoing maintenance practices
Now that you've done some ground work, it's time to start moving into longer term maintenance tasks. These are all tasks that you should do today (or as soon as possible) to get started. But for best results, make these a part of a regular maintenance schedule. We recommend setting aside time each week to help keep your computer secure.
* Back up your files. Backing up your files simply means creating a copy of your computer files that you can use in the event the originals are lost. (Accidents can happen.) To learn more read our tips for backing up information.
* Scan your files with up to date antivirus software. Use your antivirus scan tool regularly to search for potential computer viruses and worms. Also, check your antivirus program's user manual to see if you can schedule an automatic scan of your computer. To learn more, read our tips for reducing your virus risk
.
* Change your passwords. Using the same password increases the odds that someone else will discover it. Change all of your passwords regularly (we recommend monthly) to reduce your risk. Also, choose your passwords carefully. To learn more, read our tips for creating stronger passwords
.
Making a schedule
One of the best ways to help protect your computer is to perform maintenance regularly. To help you keep track, we suggest making a regular "appointment" with your computer. Treat it like you would any other appointment. Record it in your datebook or online calendar, and if you cannot make it, reschedule. Remember, you are not only helping to improve your computer, you are also helping to protect your personal information.
Getting started
Here are some basics maintenance tasks you can do today to start improving your computer's security. Be sure you make these part of your ongoing maintenance as well.
* Sign up for software update e-mail notices. Many software companies will send you e-mail whenever a software update is available. This is particularly important for your operating system (e.g., Microsoft VV!|VD0VV$® or Macintosh), your antivirus program, and your firewall.
* Register your software. If you still have registration forms for existing software, send them in. And be sure to register new software in the future. This is another way for the software manufacturer to alert you when new updates are available.
* Install software updates immediately.
When you get an update notice, download the update immediately and install it. (Remember, downloading and installing are two separate tasks.)
An ounce of prevention
A few simple steps will help you keep your files safe and clean.
* Step 1: Update your software
* Step 2: Backup your files
* Step 3: Use antivirus software and keep it updated
* Step 4: Change your passwords
Developing ongoing maintenance practices
Now that you've done some ground work, it's time to start moving into longer term maintenance tasks. These are all tasks that you should do today (or as soon as possible) to get started. But for best results, make these a part of a regular maintenance schedule. We recommend setting aside time each week to help keep your computer secure.
* Back up your files. Backing up your files simply means creating a copy of your computer files that you can use in the event the originals are lost. (Accidents can happen.) To learn more read our tips for backing up information.
* Scan your files with up to date antivirus software. Use your antivirus scan tool regularly to search for potential computer viruses and worms. Also, check your antivirus program's user manual to see if you can schedule an automatic scan of your computer. To learn more, read our tips for reducing your virus risk
.
* Change your passwords. Using the same password increases the odds that someone else will discover it. Change all of your passwords regularly (we recommend monthly) to reduce your risk. Also, choose your passwords carefully. To learn more, read our tips for creating stronger passwords
.
Making a schedule
One of the best ways to help protect your computer is to perform maintenance regularly. To help you keep track, we suggest making a regular "appointment" with your computer. Treat it like you would any other appointment. Record it in your datebook or online calendar, and if you cannot make it, reschedule. Remember, you are not only helping to improve your computer, you are also helping to protect your personal information.
COMMON FTP ERROR CODES
~~~~~~~~~COMMON FTP ERROR CODES~~~~~~~~~~
# Description
110 Restart marker reply. In this case, the text is exact and not left to the particular implementation; it must read: MARK yyyy = mmmm where yyyy is User-process data stream marker, and mmmm server's equivalent marker (note the spaces between markers and "=").
120 Service ready in nnn minutes.
125 Data connection already open; transfer starting.
150 File status okay; about to open data connection.
200 Command okay.
202 Command not implemented, superfluous at this site.
211 System status, or system help reply.
212 Directory status.
213 File status.
214 Help message.On how to use the server or the meaning of a particular non-standard command. This reply is useful only to the human user.
215 NAME system type. Where NAME is an official system name from the list in the Assigned Numbers document.
220 Service ready for new user.
221 Service closing control connection.
225 Data connection open; no transfer in progress.
226 Closing data connection. Requested file action successful (for example, file transfer or file abort).
227 Entering Passive Mode (h1,h2,h3,h4,p1,p2).
230 User logged in, proceed. Logged out if appropriate.
250 Requested file action okay, completed.
257 "PATHNAME" created.
331 User name okay, need password.
332 Need account for login.
350 Requested file action pending further information
421 Service not available, closing control connection.This may be a reply to any command if the service knows it must shut down.
425 Can't open data connection.
426 Connection closed; transfer aborted.
450 Requested file action not taken.
451 Requested action aborted. Local error in processing.
452 Requested action not taken. Insufficient storage space in system.File unavailable (e.g., file busy).
500 Syntax error, command unrecognized. This may include errors such as command line too long.
501 Syntax error in parameters or arguments.
502 Command not implemented.
503 Bad sequence of commands.
504 Command not implemented for that parameter.
530 Not logged in.
532 Need account for storing files.
550 Requested action not taken. File unavailable (e.g., file not found, no access).
551 Requested action aborted. Page type unknown.
552 Requested file action aborted. Exceeded storage allocation (for current directory or dataset).
553 Requested action not taken. File name not allowed.
# Description
110 Restart marker reply. In this case, the text is exact and not left to the particular implementation; it must read: MARK yyyy = mmmm where yyyy is User-process data stream marker, and mmmm server's equivalent marker (note the spaces between markers and "=").
120 Service ready in nnn minutes.
125 Data connection already open; transfer starting.
150 File status okay; about to open data connection.
200 Command okay.
202 Command not implemented, superfluous at this site.
211 System status, or system help reply.
212 Directory status.
213 File status.
214 Help message.On how to use the server or the meaning of a particular non-standard command. This reply is useful only to the human user.
215 NAME system type. Where NAME is an official system name from the list in the Assigned Numbers document.
220 Service ready for new user.
221 Service closing control connection.
225 Data connection open; no transfer in progress.
226 Closing data connection. Requested file action successful (for example, file transfer or file abort).
227 Entering Passive Mode (h1,h2,h3,h4,p1,p2).
230 User logged in, proceed. Logged out if appropriate.
250 Requested file action okay, completed.
257 "PATHNAME" created.
331 User name okay, need password.
332 Need account for login.
350 Requested file action pending further information
421 Service not available, closing control connection.This may be a reply to any command if the service knows it must shut down.
425 Can't open data connection.
426 Connection closed; transfer aborted.
450 Requested file action not taken.
451 Requested action aborted. Local error in processing.
452 Requested action not taken. Insufficient storage space in system.File unavailable (e.g., file busy).
500 Syntax error, command unrecognized. This may include errors such as command line too long.
501 Syntax error in parameters or arguments.
502 Command not implemented.
503 Bad sequence of commands.
504 Command not implemented for that parameter.
530 Not logged in.
532 Need account for storing files.
550 Requested action not taken. File unavailable (e.g., file not found, no access).
551 Requested action aborted. Page type unknown.
552 Requested file action aborted. Exceeded storage allocation (for current directory or dataset).
553 Requested action not taken. File name not allowed.
Sunday, January 1, 2012
Send free SMS from Facebook
- Login to your Facebook Account and go to ChatsSMS Application.
- When the Request and Permission window opens then click on Allow button.
-

- In the next window select the country and country code where you want to send the SMS.
- In the Phone Number field give your Friends mobile number and in the SMS text field type your message that you want to send.

- After this click on Send SMS button and your SMS will be delivered within few seconds.
The sent message will contain the First name of your Facebook with your precious message.
How To Disable Facebook Timeline?
How To Disable Facebook Timeline?
It works only in firefox & epic, because for it you have to install a firefox add-on named User Agent Switcher.
Download & install User Agent Switcher add-on from here.
After installing & restarting firefox: Go to Tools> Default User Agent> Internet Explorer> Click on Internet Explorer 7.
Refresh your facebook tab now & see the changes.
Note: There's no any permanent way for disabling facebook timeline, I posted only for yours convenience. I'm using it from last 2-3 months when it came for developers & it's just awesome.
For reverting back the timeline feature: Go to Tools> Internet Explorer 7> Click on Default User Agent & then refresh your facebook tab.
It works only in firefox & epic, because for it you have to install a firefox add-on named User Agent Switcher.
Download & install User Agent Switcher add-on from here.
After installing & restarting firefox: Go to Tools> Default User Agent> Internet Explorer> Click on Internet Explorer 7.
Refresh your facebook tab now & see the changes.
Note: There's no any permanent way for disabling facebook timeline, I posted only for yours convenience. I'm using it from last 2-3 months when it came for developers & it's just awesome.
For reverting back the timeline feature: Go to Tools> Internet Explorer 7> Click on Default User Agent & then refresh your facebook tab.
Subscribe to:
Comments (Atom)






